Secrets are stored as strings. If your secret is a JSON payload or similar,
remember to convert it to the correct format using
json.loads(os.environ.get("MY_JSON_SECRET")).Managing Secrets
Secrets are created, updated, and deleted in your dashboard.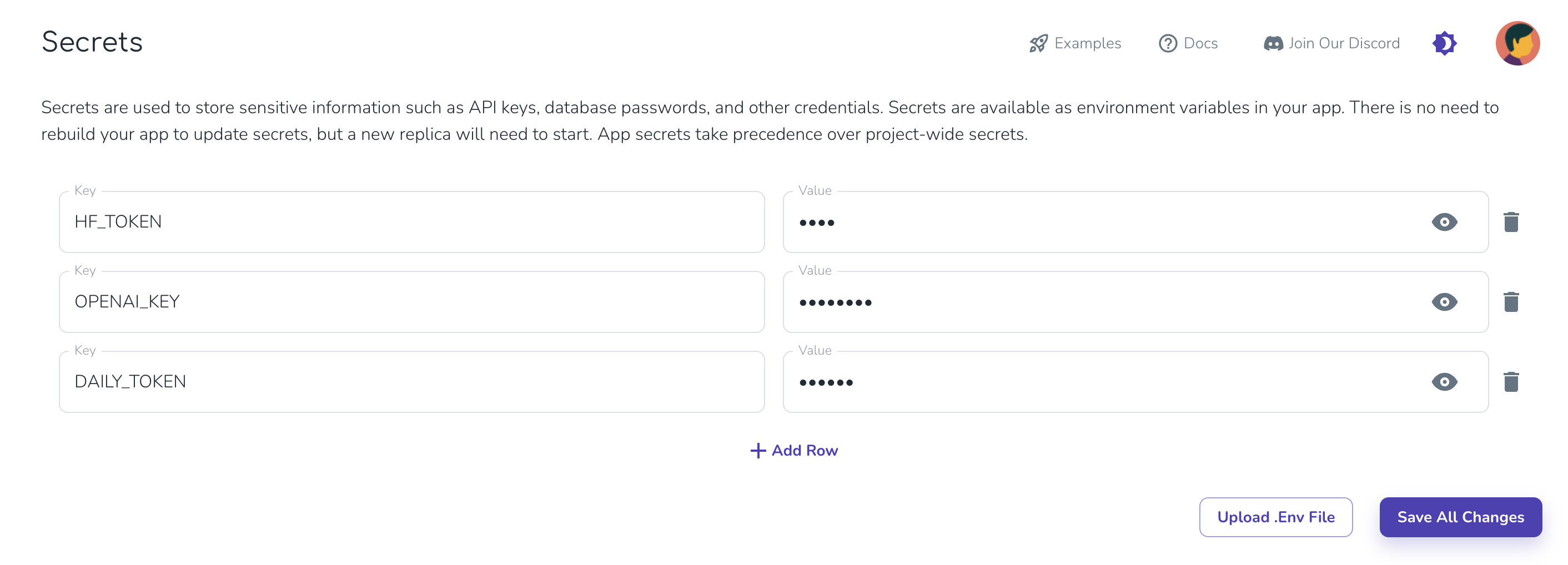
Secrets are loaded on model start. You will need to wait for your app
container to restart or deploy your app before the new secret is available.
Automatic Environment Variables
Cerebrium automatically sets the following environment variables for your app:- APP_NAME: The name of your application
- HF_HOME: Set to ‘/persistent-storage/.cache/huggingface’ for caching HuggingFace models
- PROJECT_ID: The ID of your Cerebrium project
- BUILD_ID: The unique identifier for the current build
The app_id is a composite of PROJECT_ID + ’_’ + APP_NAME.
Local Development
When developing locally, you can use an.env file to store your secrets. Later, you can add these secrets to your project from the dashboard.